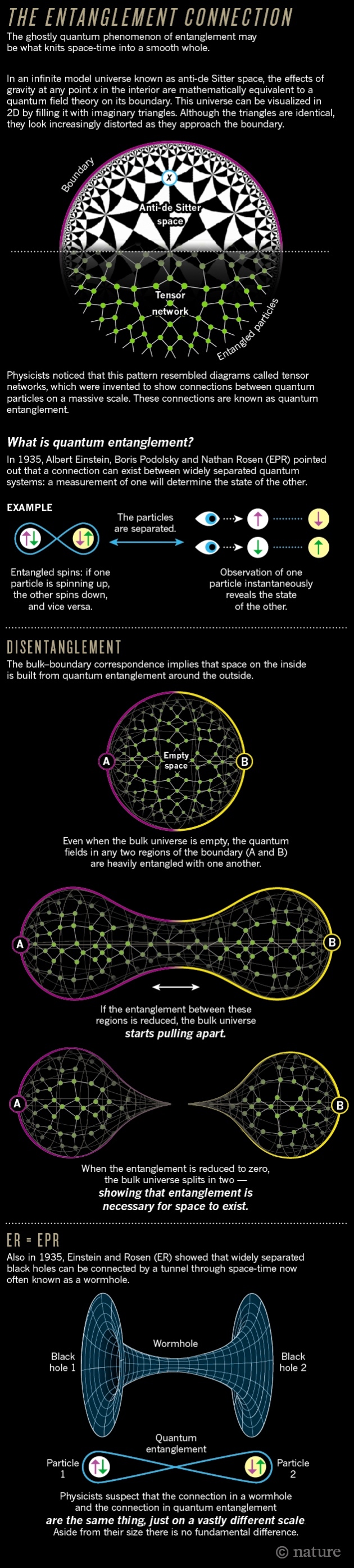
(no subject)
Sep. 11th, 2017 01:48 am(via Vlad) An instructive interview that shows how people make mental mistakes by extrapolating technology solutions with "more-of-the-same" thinking:
http://archive.is/6M8mg#selection-1375.7-1381.541
Basically, she assumes that data security and hardware capacity/budget are "entangled" linear orders.
also see https://timelets.dreamwidth.org/682944.html
upd: the alleged exploit https://qz.com/1073221/the-hackers-who-broke-into-equifax-exploited-a-nine-year-old-security-flaw/
http://archive.is/6M8mg#selection-1375.7-1381.541
“
We spend our time looking for threats against a company. We look for things that might be active inside the company that would cause us concern, and then of course we look to respond—detecting, containing, and deflecting those threats as much as possible while at the same time keeping in mind that our executives and board of directors always want to know what's going on with security in the company.
Generically, every breach has the big data problem. For example, in a malware incident that results in a breach, the malware comes in and spreads across the environment.
When that scope [of investigation] expands, the security team typically has to deal with a sudden increase in big data -- logs, alerts, etc. -- making budget planning critical. Right now I'm planning my budget for next year, and I hope I ask for enough disk space and computing power so that the infrastructure is prepared for future attacks. ... Burst capacity is really critical for the security team who needs to find answers quickly.
Basically, she assumes that data security and hardware capacity/budget are "entangled" linear orders.
also see https://timelets.dreamwidth.org/682944.html
upd: the alleged exploit https://qz.com/1073221/the-hackers-who-broke-into-equifax-exploited-a-nine-year-old-security-flaw/